
| OpenSSHfor Windows |
The OpenSSH website is located at www.openssh.com
This website hosts a Windows installer package of Openssh for Windows that is actively maintained and current.
The sshwindows package hasn't been maintained for a long timeand is woefully out of date. I've been rolling my ownversions of this installer for quite a while and figured others mightfind this useful as well.
I'll walk you through installationand setup of the OpenSSH package forWindows. First download the latest version (or the version of your choice), and head to the bottom of the page for a quick walk-thru
If you are looking for OpenSSH binaries for Windows 2000, XP, or 2003, head over to the OpenSSH installers for Windows 2000/XP/2003 pagefor links to the latest binaries that will work with those particular operating systems.
If you are looking for older OpenSSH binaries that have been hosted on this site in the past, head over to the older OpenSSH installer page.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~NOTE~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
As was pointed out, the Windows OpenSSH installer could be even more useful to people if it had additional language support. To contribute, download Descriptions.zip. Open the zip and edit Descriptions.nsi and email the updated language descriptions (Descriptions.nsi) to me at admin<AT>mls-software.com with a note as to how you would like to be credited and I'll get that included in the release. First to respond will get the credit, and I'll cross languages off the list as they come in. Based on the download history, the following countries primary languages would be the most useful: China, Japan, India, Russia, Italy, Ukraine, Netherlands. Languages currently supported: German - creopard.de, Danish - Tox, Portuguese (Brazil) - HackerOrientado, Spanish - zaquintar, French - MirrorBrain, Chinese_Simple - Wair56. Thanks for your help.~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~NOTE~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
New VersionOpenSSH 8.5p1-1
This is an updated OpenSSH 8.5p1-1 installer for both x86 and x64 binaries. This version includes ssh-sk-helper.exe, cygfido2-1.dll, and cygcbor-0.dll (which was missing last time) so I hope it provides Yubikey support (I have no way to test that) The random password that is generated WILL NOT work with Windows Server causing the service to be unable to start - you MUST REPLACE THAT PASSWORD WITH SOMETHING THAT MEETS THE COMPLEXITY REQUIREMENTS OF A SERVER. Frankly, that password should be replaced in all cases...but people tend to be lazy :-)
| Version | Windows x86 | Windows x64 | | OpenSSH 8.5p1-1 | setupssh-8.5p1-1.exe
SHA1=b280544abbfa5725486d5e3de6bc26c53cbf17d9 | | (Optional) Cygwin Source Files | cygwin_source.32.85p1-1.zip
SHA1=3e647607ebd382caeb519ee5b4beb4742d191d42 | cygwin_source.64.85p1-1.zip
SHA1=9d27016e2367195ee5b4349f0165f7f12e3633c0 | | (Optional) Installer Source Files | installer_source_files.85p1-1.zip
SHA1=6a39ab82bf8e61a39e4a0562ce70426d745ce527 |
Older VersionsOpenSSH 8.4p1-2
This is an updated OpenSSH 8.4p1-2 installer for both x86 and x64 binaries. This version includes ssh-sk-helper.exe and cygfido2-1.dll so I hope it provides Yubikey support (I have no way to test that) The random password that is generated WILL NOT work with Windows Server causing the service to be unable to start - you MUST REPLACE THAT PASSWORD WITH SOMETHING THAT MEETS THE COMPLEXITY REQUIREMENTS OF A SERVER. Frankly, that password should be replaced in all cases...but people tend to be lazy :-)
| Version | Windows x86 | Windows x64 | | OpenSSH 8.4p1-2 | setupssh-8.4p1-2.exe
SHA1=18d54d8a551cdcb438e3316d43d830dda3eb1ff4 | | (Optional) Cygwin Source Files | cygwin_source.32.84p1-2.zip
SHA1=7bbd012931c4edac3bc219c6aa27278e3e114823 | cygwin_source.64.84p1-2.zip
SHA1=214aa4028efecd10ef74b59463bf6ae2e4ca4288 | | (Optional) Installer Source Files | installer_source_files.84p1-2.zip
SHA1=a6690427de2cb0e0e6bd1f04884efe3f975448b1 |
OpenSSH 8.4p1-1
This is an updated OpenSSH 8.4p1-1 installer for both x86 and x64 binaries. Happy Halloween! The random password that is generated WILL NOT work with Windows Server causing the service to be unable to start - you MUST REPLACE THAT PASSWORD WITH SOMETHING THAT MEETS THE COMPLEXITY REQUIREMENTS OF A SERVER. Frankly, that password should be replaced in all cases...but people tend to be lazy :-)
| Version | Windows x86 | Windows x64 | | OpenSSH 8.4p1-1 | setupssh-8.4p1-1.exe
SHA1=e94e203f40bcd1e1e63fda0dab8788f605df1eb8 | | (Optional) Cygwin Source Files | cygwin_source.32.84p1-1.zip
SHA1=e512607abaf716a17b303f978c30cbfbcc84f108 | cygwin_source.64.84p1-1.zip
SHA1=857a32a06c960a24dc2c9b0a6601132e69ef2a1c | | (Optional) Installer Source Files | installer_source_files.84p1-1.zip
SHA1=69c15a0ef4a252abd63154bc4b66cacc060bd82a |
OpenSSH 8.3p1-1
This is an updated OpenSSH 8.3p1-1 installer for both x86 and x64 binaries. The random password that is generated WILL NOT work with Windows Server causing the service to be unable to start - you MUST REPLACE THAT PASSWORD WITH SOMETHING THAT MEETS THE COMPLEXITY REQUIREMENTS OF A SERVER. Frankly, that password should be replaced in all cases...but people tend to be lazy :-) I have updated the libraries I'm using so now Chinese and Russian language translations should show up correctly.
| Version | Windows x86 | Windows x64 | | OpenSSH 8.3p1-1 | setupssh-8.3p1-1.exe
SHA1=e6a5b9d5a514cd5a9236ab746c8dc497a47d1cf1 | | (Optional) Cygwin Source Files | cygwin_source.32.83p1-1.zip
SHA1=9e4e38901f9b89a17478ba59186bff54abed9daf | cygwin_source.64.83p1-1.zip
SHA1=94e598d29f2744fa825786805abb14baf8f369bf | | (Optional) Installer Source Files | installer_source_files.83p1-1.zip
SHA1=6466b403394fd98de01fbd32d5bfa924f7d29356 |
OpenSSH 8.2p1-1
This is an updated OpenSSH 8.2p1-1 installer for both x86 and x64 binaries. The random password that is generated WILL NOT work with Windows Server causing the service to be unable to start - you MUST REPLACE THAT PASSWORD WITH SOMETHING THAT MEETS THE COMPLEXITY REQUIREMENTS OF A SERVER. Frankly, that password should be replaced in all cases...but people tend to be lazy :-) I also missed a file last time that caused you not to be able to connect to the sshd service running on your Windows system - that has been remedied (cygwin-console-helper.exe). I had hoped to fix Chinese and Russian language translations so they showed up correctly, however, there are some bugs in the unicode library that I updated/ported that I haven't fixed yet. Thanks to the Simon H. who sent me some clues on how to fix that issue. I should hopefully have this fixed by next rev.
| Version | Windows x86 | Windows x64 | | OpenSSH 8.2p1-1 | setupssh-8.2p1-1.exe
SHA1=6d423cf4b01332a84bdf558fa6f57105122139ee | | (Optional) Cygwin Source Files | cygwin_source.32.82p1-1.zip
SHA1=49733708b9b6e15fc9b634544236502134687ce6 | cygwin_source.64.82p1-1.zip
SHA1=469acd08d163dfb1da13cc511b917e9684defd0f | | (Optional) Installer Source Files | installer_source_files.82p1-1.zip
SHA1=997e3517ff934f6f2d41893704add7ed730eed43 |
OpenSSH 8.1p1-1
This is an updated OpenSSH 8.1p1-1 installer for both x86 and x64 binaries. The random password that is generated WILL NOT work with Windows Server causing the service to be unable to start - you MUST REPLACE THAT PASSWORD WITH SOMETHING THAT MEETS THE COMPLEXITY REQUIREMENTS OF A SERVER. Frankly, that password should be replaced in all cases...but people tend to be lazy :-) I tweaked the default firewall rules based on a suggestion from John B. Please note - for some reason the Chinese and Russian language translations aren't showing up in my drop down for languages. If anybody knows how to fix that...I'd take a hint. Also, the Russian language translations don't show up as Russian characters, I have strange symbols - as such, I don't know that the file I was provided actually is correct. Any Russian speakers care to review the Decriptions.nsi from the source file and provide some verification or update that would be appreciated. I use Notepad++ as my editor so please check out that file with that editor. Thanks!
| Version | Windows x86 | Windows x64 | | OpenSSH 8.1p1-1 | setupssh-8.1p1-1.exe
SHA1=9d6e5f5e36899ec4e8391c368c496796b36c8a62 | | (Optional) Cygwin Source Files | cygwin_source.32.81p1-1.zip
SHA1=1787f3f2de09b55d2904cfd6041040e9c327a56c | cygwin_source.64.81p1-1.zip
SHA1=8fcdfaf65bd655b7e64789f80da0ca406b07e5d8 | | (Optional) Installer Source Files | installer_source_files.81p1-1.zip
SHA1=de054b8dc29bf19407be14f49dea5859c3d85937 |
OpenSSH 8.0p1-2
This is an updated OpenSSH 8.0p1-2 installer for both x86 and x64 binaries. The random password that is generated WILL NOT work with Windows Server causing the service to be unable to start - you MUST REPLACE THAT PASSWORD WITH SOMETHING THAT MEETS THE COMPLEXITY REQUIREMENTS OF A SERVER. Frankly, that password should be replaced in all cases...but people tend to be lazy :-) I incorporated some suggestions from Bill S. Russian langauge translations added (anonymous contributor). Please note - for some reason the Chinese and Russian language translations aren't showing up in my drop down for languages. If anybody knows how to fix that...I'd take a hint. Also, the Russian language translations don't show up as Russian characters, I have strange symbols - as such, I don't know that the file I was provided actually is correct. Any Russian speakers care to review the Decriptions.nsi from the source file and provide some verification or update that would be appreciated. I use Notepad++ as my editor so please check out that file with that editor. Thanks!
| Version | Windows x86 | Windows x64 | | OpenSSH 8.0p1-2 | setupssh-8.0p1-2.exe
SHA1=4cdf9628aab704f2b086008857430456b2333a35 | | (Optional) Cygwin Source Files | cygwin_source.32.80p1-2.zip
SHA1=f3a73942fd957576f044df52c0cb51e9cbad5f42 | cygwin_source.64.80p1-2.zip
SHA1=b59ead95617474047680bad22b553ad31400cd9a | | (Optional) Installer Source Files | installer_source_files.80p1-2.zip
SHA1=55622d5efc5614720001d9033f93621710aa68fe |
OpenSSH 7.9p1-1
This is an updated OpenSSH 7.9p1-1 installer for both x86 and x64 binaries. The random password that is generated WILL NOT work with Windows Server causing the service to be unable to start - you MUST REPLACE THAT PASSWORD WITH SOMETHING THAT MEETS THE COMPLEXITY REQUIREMENTS OF A SERVER. Frankly, that password should be replaced in all cases...but people tend to be lazy :-) No new languages this release - more languages would be welcome.
| Version | Windows x86 | Windows x64 | | OpenSSH 7.9p1-1 | setupssh-7.9p1-1.exe
SHA1=64425b56f890cbf51ddf4a9292b02b06df70487e | | (Optional) Cygwin Source Files | cygwin_source.32.79p1-1.zip
SHA1=ceb6f1a8669f5693ac483c542cde7789f9bf5727 | cygwin_source.64.79p1-1.zip
SHA1=53f63865032025785bc3ade8801f4a1d95e91d82 | | (Optional) Installer Source Files | installer_source_files.79p1-1.zip
SHA1=6294c1741e30155adce2071f61c2bc419eb953e0 |
OpenSSH 7.8p1-1
This is an updated OpenSSH 7.8p1-1 installer for both x86 and x64 binaries. The random password that is generated WILL NOT work with Windows Server causing the service to be unable to start - you MUST REPLACE THAT PASSWORD WITH SOMETHING THAT MEETS THE COMPLEXITY REQUIREMENTS OF A SERVER. Frankly, that password should be replaced in all cases...but people tend to be lazy :-) No new languages this release - more languages would be welcome.
| Version | Windows x86 | Windows x64 | | OpenSSH 7.8p1-1 | setupssh-7.8p1-1.exe
SHA1=ef12f4c3148e95134614e2dd0a2b71cedb545027 | | (Optional) Cygwin Source Files | cygwin_source.32.78p1-1.zip
SHA1=f9aa5f8fb2cd4d98f3974ceedc7bb0e8287d5717 | cygwin_source.64.78p1-1.zip
SHA1=d1dc693ce9fce626b1490f2a553391af3faa25a8 | | (Optional) Installer Source Files | installer_source_files.78p1-1.zip
SHA1=70b71a8f9f8b3cab7a3e739d77026a75ec69227c |
OpenSSH 7.7p1-1
This is an updated OpenSSH 7.7p1-1 installer for both x86 and x64 binaries. The random password that is generated WILL NOT work with Windows Server causing the service to be unable to start - you MUST REPLACE THAT PASSWORD WITH SOMETHING THAT MEETS THE COMPLEXITY REQUIREMENTS OF A SERVER. Frankly, that password should be replaced in all cases...but people tend to be lazy :-) Finally, this release includes language support for Simplified Chinese - more languages would be welcome.
| Version | Windows x86 | Windows x64 | | OpenSSH 7.7p1-1 | setupssh-7.7p1-1.exe
SHA1=ec1e5644314a335b70b45bb6254ec63b8bd50dcb | | (Optional) Cygwin Source Files | cygwin_source.32.77p1-1.zip
SHA1=40f715eaedcdd0a22787e22b9e1dbdb59b8ca93a | cygwin_source.64.77p1-1.zip
SHA1=b09ffd951f53b167d5130aca325035a5ce99232e | | (Optional) Installer Source Files | installer_source_files.77p1-1.zip
SHA1=7c8c95be73ad1d97b2b03e98aeaf7757ea026b95 |
OpenSSH 7.6p1-1
This is an updated OpenSSH 7.6p1-1 installer for both x86 and x64 binaries. There was a major change to this release - for security reasons the password associated with the sshd_server account is randomly generated (instead of D0ntGu3$$M3). You may change the password during the install process, but it was brought to my attention that many people probably weren't changing the D0ntGu3$$M3 password and that was of course a HUGE security risk. Finally, this release includes language support for Spanish and French - more languages would be welcome.
| Version | Windows x86 | Windows x64 | | OpenSSH 7.6p1-1 | setupssh-7.6p1-1.exe
SHA1=31cdffb879ab73c8ecbcbccab6f3c0f882ab6548 | | (Optional) Cygwin Source Files | cygwin_source.32.76p1-1.zip
SHA1=42dbdbc82cca7471b88c422164b911c0951136e5 | cygwin_source.64.76p1-1.zip
SHA1=4a7dbecfa83bfa87e3005ee6a811b590c24fbf37 | | (Optional) Installer Source Files | installer_source_files.76p1-1.zip
SHA1=8409388f0d3ca1c1402d99d2f111ea84bb0dfae9 |
OpenSSH 7.5p1-1
This is an updated OpenSSH 7.5p1-1 installer for both x86 and x64 binaries. There was a major change to this release - for security reasons the server (sshd) MUST run with privilege seperation. As such, the installer and sshd_config file were updated to support this change. This brings with it a caveat - the installer has a default password for the sshd_server account (which is required for privilege seperation) - the password is D0ntGu3$$M3. YOU MUST PICK YOUR OWN PASSWORD FOR YOUR SYSTEM IF YOU ARE USING THE SERVER. I also changed the installer to install the server by default UNLESS you specify only the client via the installer or via a /clientonly=1 if you are using the command line switches. The rysnc command was also added to the binary directory. The final change was the removal of the pop-up windows that showed up during install - this change has been requested in the past and was requested again -- I have removed the windows as they just clutter things up. Finally, this release includes language support for German, Danish, and Portuguese (Brazil) - more languages would be welcome.
| Version | Windows x86 | Windows x64 | | OpenSSH 7.5p1-1 | setupssh-7.5p1-1.exe
SHA1=199ad10d578075dfe9651daa53e6f93cf6254486 | | (Optional) Cygwin Source Files | cygwin_source.32.75p1-1.zip
SHA1=0f458482df2da43e79327f1fb28a83fd8263e0b8 | cygwin_source.64.75p1-1.zip
SHA1=3d66606d20bb3b4b2e0a5c902978b9d2a7787b48 | | (Optional) Installer Source Files | installer_source_files.75p1-1.zip
SHA1=ccc1a10f0565b1579cc6124082a48ffda2d24d98 |
OpenSSH 7.4p1-1
This is an updated OpenSSH 7.4p1-1 installer for both x86 and x64 binaries. This release includes language support for German and Danish - more languages would be welcome. Includes a fix to the x86 install directory.
| Version | Windows x86 | Windows x64 | | OpenSSH 7.4p1-1 | setupssh-7.4p1-1.exe
SHA1=245a5999d3f4c944c7a0d7fbf460450f91efa6d9 | | (Optional) Cygwin Source Files | cygwin_source.32.74p1-1.zip
SHA1=cc1b4228d2ad410d1c35c4332d186d3b3f94bb4b | cygwin_source.64.74p1-1.zip
SHA1=1b80feab0a0551052ab06dd420755104ccfcf52c | | (Optional) Installer Source Files | installer_source_files.74p1-1.zip
SHA1=c3a2b9fc008302d78d24fb2f5271ab977ef8fc95 |
OpenSSH 7.3p1-2
This is an updated OpenSSH 7.3p1-2 installer for both x86 and x64 binaries. This includes a small fix to the uninstall $INSTDIR variable so a user selected installation directory is used (Thanks Jacob T for pointing out the error).
| Version | Windows x86 | Windows x64 | | OpenSSH 7.3p1-1 | setupssh-7.3p1-2.exe
SHA1=d2e8779040ad3e0c932f66bef03bc97a8f5bdda2 | | (Optional) Cygwin Source Files | cygwin_source.32.73p1-2.zip
SHA1=1ee0c9cc3d5588cb544922e237b73cec738081a6 | cygwin_source.64.73p1-2.zip
SHA1=ce9205bab22dab8f3d31e2711d2e3840bd4996ec | | (Optional) Installer Source Files | installer_source_files.73p1-2.zip
SHA1=9b2872d248df358a3783a0436c952b7e5088f0e7 |
OpenSSH 7.3p1-1
This is an updated OpenSSH 7.3p1-1 installer for both x86 and x64 binaries. This includes a small fix to the silent install $INSTDIR variable so a user selected installation directory is not overwritten.
| Version | Windows x86 | Windows x64 | | OpenSSH 7.3p1-1 | setupssh-7.3p1-1.exe
SHA1=ff5f2ea18e9f2728a2944e4d0940a68706aaf096 | | (Optional) Cygwin Source Files | cygwin_source.32.73p1-1.zip
SHA1=3634a90a51bc850b75b80b44ec9f7e8adfdb73fd | cygwin_source.64.73p1-1.zip
SHA1=749adcd99673e20eaad52978084c886cd87eea4f | | (Optional) Installer Source Files | installer_source_files.73p1-1.zip
SHA1=e416082bdc85633f2f9842992e7b4fd7df9cc5fa |
OpenSSH 7.2p2-1-v1
This is an updated OpenSSH 7.2p2-1-v1 installer (no changes to the version of OpenSSH) for both x86 and x64 binaries. I included an incorrect cygwin1.dll for x64 builds causing both ls.exe and mv.exe to fail.
| Version | Windows x86 | Windows x64 | | OpenSSH 7.2p2-1-v1 | setupssh-7.2p2-1-v1.exe
SHA1=4eff121021e5551dc762db3fb6d82ad9a989c2b5 | | (Optional) Cygwin Source Files | cygwin_source.32.72p2-1-v1.zip
SHA1=50e22b1e6c365345e22c4b75f94a286d0557493f | cygwin_source.64.72p2-1-v1.zip
SHA1=1cfff3a5f65166652c02a8f5247fe9936efe9f85 | | (Optional) Installer Source Files | installer_source_files.72p2-1-v1.zip
SHA1=9a4c14b4d0c2e89dbd1d7cc1030093525cb8b5e9 |
OpenSSH 7.2p2-1
This is an updated OpenSSH 7.2p2-1 installer for both x86 and x64 binaries.
| Version | Windows x86 | Windows x64 | | OpenSSH 7.2p2-1 | setupssh-7.2p2-1.exe
SHA1=5cf36aa793c0116d9bba765ae6152531e14772f4 | | (Optional) Cygwin Source Files | cygwin_source.32.72p2-1.zip
SHA1=982f7a1067da70928fb2cccc6fd5ada57a192734 | cygwin_source.64.72p2-1.zip
SHA1=5070caf339ae81ab6379deee2696e84fe343d72e | | (Optional) Installer Source Files | installer_source_files.72p2-1.zip
SHA1=cbd868e9517ca4ef334f319e86c2099e04fc6e5b |
OpenSSH 7.2p1-1
This is an updated OpenSSH 7.2p1-1 installer for both x86 and x64 binaries. I made a couple small tweaks - spaces are allowed in the service password and using large passwords should not cause a prompt.
| Version | Windows x86 | Windows x64 | | OpenSSH 7.2p1-1 | setupssh-7.2p1-1.exe
SHA1=a2b26af4613e66ca3d779c9bf1eb7f787ada6c69 | | (Optional) Cygwin Source Files | cygwin_source.32.72p1-1.zip
SHA1=909e221c6d8c25937882650720b3f9489bef1322 | cygwin_source.64.72p1-1.zip
SHA1=dc8dbb0c5cb068e733625625fbaecbbbd6312cac | | (Optional) Installer Source Files | installer_source_files.72p1-1.zip
SHA1=54f38a2fc84b5fb7c17316c0b54a057570248fe1 |
OpenSSH 7.1p2-1
This is an updated OpenSSH 7.1p1-1 installer for both x86 and x64 binaries. I also took this opportunity to clean up the files to only the minimal dependencies. Let me know if you run into any missing file warnings.
| Version | Windows x86 | Windows x64 | | OpenSSH 7.1p2-1 | setupssh-7.1p2-1.exe
SHA1=2f304d562e8b9c7c81c0fac80fa939c730165b53 | | (Optional) Cygwin Source Files | cygwin_source.32.71p2-1.zip
SHA1=4de4bb82937b46bf8964b4c9a47b346dbac5eb54 | cygwin_source.64.71p2-1.zip
SHA1=9a0f7b94e1686458e310dc72df8436e49d24c6a7 | | (Optional) Installer Source Files | installer_source_files.71p2-1.zip
SHA1=6493ce40ac5c89df836fff128132e54a9cd0438e |
OpenSSH 7.1p1-1
This is an updated OpenSSH 7.1p1-1 installer for both x86 and x64 binaries.
| Version | Windows x86 | Windows x64 | | OpenSSH 7.1p1-1 | setupssh-7.1p1-1.exe
SHA1=131e027050fb8b985f564e6b5c3b0d054d703dbb | | (Optional) Cygwin Source Files | cygwin_source.32.71p1-1.zip
SHA1=e5ba369adeb9edadae40a749373eb16ae9f1341a | cygwin_source.64.71p1-1.zip
SHA1=d94b3d9a56a7741aa130af6a7157b64ade0d9c40 | | (Optional) Installer Source Files | installer_source_files.71p1-1.zip
SHA1=26d70ce5da4961b5a13af2aa3d5b9b384ad214be |
Once you've downloaded the executable, start it up to be greeted withthe OpenSSH splash screen followed by the welcome and license screen. You can select the defaults all the way through theinstallation process if desired - these should work for mostintallations:
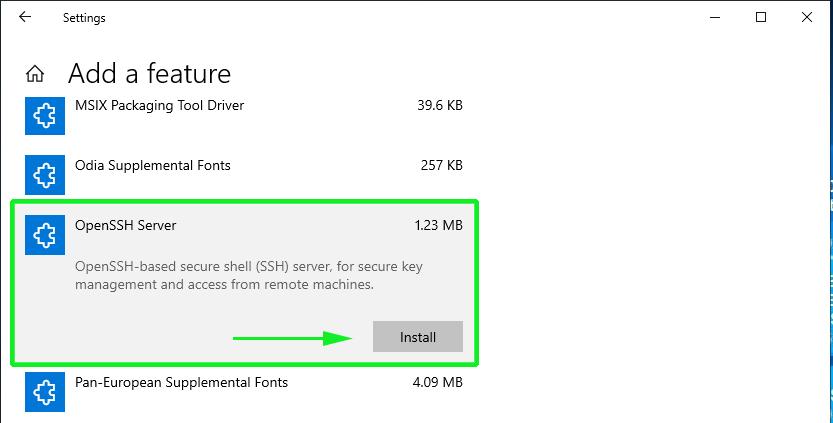
The first point where you get to make some choices is the choosecomponent dialog.
Select
Client - to install the sshclient command line tools (if you want to connect to other ssh servers
Server - to install the ssh server command line application (if youwant to provide an ssh server for others to connect to)
Start Menu Shortcuts - a few start menushortcuts
Thenext screen that requires some explanation is the 'Choose account underwhich to execute SSHD'. The SSH Daemon (SSHD) can run aseitherLocal_System or SSHD_Server. If you are using Windows Server (2003/2008/2008R2/etc.)youwill likely have to run this as SSHD_Server, however all others shouldbe able to run this as Local_System. The default passwordthat isfilled in for you is 'D0ntGu3$$M3' - I would recommend changing it! You can change thislater byusing the Services Control Panel.
If you choose 'Run as SSHD_Server', then you will be presented with theprivilege seperation option.
In general, itshould be OK to not use priviledge seperation unless you are runningWindows 2003.
Ifyou are running the sshd server, select the port. The defaultport for ssh is 22, however you may select whatever you want (but thenyou'll have to pass that in as on -p option when you connect)
You may now select the keysize. The default keysize of 2048 is probably sufficient, however ifyou are truly concerned about your network privacy 4096 would be a good next choice.
You canconfigure ssh for either local users or domain users. Thisdetermines how the password file is setup and you should probablychooseLocal users.
OpenSSH will begin to install and configure itself for your system.
At this point, openssh is setup and configured for your system. Totry this out, open up a command prompt (cmd.exe) and try:
ssh -v (For OpenSSH 6.3 and below)
ssh -V (For OpenSSH 6.4 and above)
which will show you the version information.
If youinstalled the openssh server, it will start automatically after theinstallation completes.
You may also open up a command prompt with administratorpriviledges and try:
net start opensshd
which should cause the opensshd daemon service to start
To stop the service (if/when you want to):
net stop opensshd
You can also stop/start the openssh service from the Services controlpanel applet.
If you experience problems with the service, look in /var/log as itmight have a clue why the service is failing to start.
The original source code for sshwindowscame from SourceForge.net.
|
|
OpenSSH 8.6 is now available. The 'ssh-rsa' signature scheme, which usesthe SHA-1 hash algorithm, will be disabled by default in the nearfuture. '
This is an updated OpenSSH 7.5p1-1 installer for both x86 and x64 binaries. There was a major change to this release - for security reasons the server (sshd) MUST run with privilege seperation. As such, the installer and sshdconfig file were updated to support this change. Fix OpenSSH Server connection drops out after few minutes of inactivity. First, log into the remote server and then open your /etc/ssh/sshdconfig file: # vi /etc/ssh/sshdconfig Modify setting as follows: ClientAliveInterval 30 ClientAliveCountMax 5 Where.
Note that the deactivation of 'ssh-rsa' signatures does notnecessarily require cessation of use for RSA keys. In the SSH protocol,keys may be capable of signing using multiple algorithms. In particular,'ssh-rsa' keys are capable of signing using 'rsa-sha2-256' (RSA/SHA256),'rsa-sha2-512' (RSA/SHA512) and 'ssh-rsa' (RSA/SHA1). Only the last ofthese is being turned off by default.'
| From: | Damien Miller <djm-AT-cvs.openbsd.org> |
| To: | lwn-AT-lwn.net |
| Subject: | Announce: OpenSSH 8.6 released |
| Date: | Sun, 18 Apr 2021 18:53:14 -0600 |
| Message-ID: | <94b0350a0f8a1fac@cvs.openbsd.org> |
(Log in to post comments)
OpenSSH 8.6 released
Posted Apr 20, 2021 7:14 UTC (Tue) by wtarreau (subscriber, #51152) [Link]
The incessant switch between algorithms is a real pain. Initially we were all using RSA. Then we were told RSA was bad and that DSA had to be used instead. We all switched to DSA. Then DSA was deamed bad forcing many of us to turn back to RSA after facing connection issues on their machines, but with larger keys this time. Then ED25519 started to appear but is still not enabled on a wide number of already installed machines (typically the machines we have in our respective basements). Now RSA's dead again...
SSH is widely used to connect, but not only where extreme security is required, simply where you need to connect (i.e. the old server on your local network, where it replaced telnet+ftp). In such situations removing support for algorithms breaks the connectivity, makes backups fail, and causes lots of grief. I think that clients should not completely remove support for no-so-old algorithm but instead require an extra option like '--insecure' or something like this. Because clearly if I can't connect anymore to some of my old machines, I'll go back to telnet, which never broke accessibility in 40 years. And I do think that SSH is better than telnet, even with older keys that a neighbor could fake for $50k to intercept my connection on my local network just to send me a 'you're pwned' banner when I connect...
OpenSSH 8.6 released
Posted Apr 20, 2021 7:39 UTC (Tue) by cjwatson (subscriber, #7322) [Link]
No, RSA is not dead. There is a warning (which has been in the OpenSSH release notes for several releases, so I don't know why LWN picked it for a pull quote) that a particular signature scheme used with RSA is deprecated, but RSA keys will still work just fine even after that scheme is eventually removed.
OpenSSH 8.6 released
Posted Apr 20, 2021 8:21 UTC (Tue) by Sesse (subscriber, #53779) [Link]
RSA keys yes, but that isn't the problem: SSHing to your switch, where you cannot change the sshd implementation, is. (Keys can, after all, be replaced pretty easily!) This is a huge pain, and has only been accelerating in the last decade.
Unable to negotiate with <ip> port 22: no matching key exchange method found. Their offer: diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha1
I sometimes keep a machine on oldstable or oldoldstable around, so that I can have an older ssh(1) binary to SSH to stuff with…
OpenSSH 8.6 released
Posted Apr 20, 2021 9:20 UTC (Tue) by dottedmag (subscriber, #18590) [Link]
ssh -oKexAlgorithms=diffie-hellman-group-exchange-sha1 oldbox?
OpenSSH 8.6 released
Posted Apr 20, 2021 9:32 UTC (Tue) by Sesse (subscriber, #53779) [Link]
Works for that case, yes, but not for all others. E.g. I have devices that only accept SSHv1. Terribly insecure, yes, but the real alternative is telnet.
OpenSSH 8.6 released
Posted Apr 20, 2021 10:38 UTC (Tue) by Cyberax (✭ supporter ✭, #52523) [Link]
Just build a 'crapssh' utility then, it's pretty easy to do that using old sources of OpenSSH.
OpenSSH 8.6 released
Posted Apr 20, 2021 8:41 UTC (Tue) by Vipketsh (guest, #134480) [Link]
A better example is some old(er) networking equipment, like a managed switch. These things are often disowned by their manufacturers so no hope to getting any update with more recent authentication schemes but the equipment works perfectly well for its intended function. I would be happy if they disabled rsa-ssh on the server and put it into some last-resort-fallback list on the client when negotiating the scheme.
It would be great if security people today would understand that security is a function of *three* things: Confidentiality, Integrity and *Availability*. Clearly availability is being reduced here for no gain in Integrity.
OpenSSH 8.6 released
Posted Apr 20, 2021 10:14 UTC (Tue) by hkario (subscriber, #94864) [Link]
> Clearly availability is being reduced here for no gain in Integrity.Openssh Server Config Tool
That's your opinion, not shared by wider security community.
Look for SSH Downgrade Attacks to learn why.
OpenSSH 8.6 released
Posted Apr 20, 2021 10:43 UTC (Tue) by pizza (subscriber, #46) [Link]
> That's your opinion, not shared by wider security community.> Look for SSH Downgrade Attacks to learn why.Sure, and the net result of this 'improved security' is 'SSH downgrade to telnet'
Mission accomplished, I guess.
OpenSSH 8.6 released
Posted Apr 20, 2021 11:04 UTC (Tue) by hkario (subscriber, #94864) [Link]
First, count number of people that use SSH daily with modern ciphers and count how many people need to use long insecure protocols like SSHv1.
Second, you aren't secure with SSHv1, at least with telnet you're not lying to yourself that you are. So there's a chance that you'll do something about it. That is improved security: real, not apparent.
OpenSSH 8.6 released
Posted Apr 20, 2021 11:32 UTC (Tue) by pizza (subscriber, #46) [Link]
> That is improved security: real, not apparent.What is 'real, improved' over dropping the barrier of attack from $50K to $0?
At $50K, you're only going to be vulnerable to larger criminal enterprises and nation-states that are specifically going after _you_. But at $0 you're open to every script kiddie on the internet with a copy of nmap.
Your argument is equivalent to getting rid of the front doors on houses because they're easy to open.
OpenSSH 8.6 released
Posted Apr 20, 2021 11:40 UTC (Tue) by hkario (subscriber, #94864) [Link]
OpenSSH 8.6 released
Posted Apr 22, 2021 17:39 UTC (Thu) by jschrod (subscriber, #1646) [Link]
No, you don't understand him.
It seems that there are a lot of ssh use cases that you haven't experienced yet, especially in the network devices realm.
OpenSSH 8.6 released
Posted Apr 20, 2021 15:03 UTC (Tue) by foom (subscriber, #14868) [Link]
If you have a device that's so old it only runs sshv1 -- which presumably means it hasn't been updated in 20 years -- does it really matter what protocol you use to connect to it?
It's there any chance it isn't exploitable via some well known security vulnerabilities? Quite possibly even ones which have been nicely packaged into a one-click exploit toolkit, and a may be just as easy to 'login' with as an ssh client...
OpenSSH 8.6 released
Posted Apr 20, 2021 14:03 UTC (Tue) by epa (subscriber, #39769) [Link]
I once patched ssh 1.x to add a 'none' cipher, sending data over the wire unencrypted. That helped get usable performance on a 16MHz 386SX. I'd much rather run ssh and sshd, even without encryption, than go back to telnet.
OpenSSH 8.6 released
Posted Apr 20, 2021 16:53 UTC (Tue) by Vipketsh (guest, #134480) [Link]
Disabling the weak algorithm on the server thwarts the downgrade attack, from what I understand (no expert though so feel free to correct me). It then doesn't make sense to disabled it on the client side.
OpenSSH 8.6 released
Posted Apr 20, 2021 12:21 UTC (Tue) by pabs (subscriber, #43278) [Link]
Do these switches not support standard Linux distros?
OpenSSH 8.6 released
Posted Apr 20, 2021 16:55 UTC (Tue) by floppus (subscriber, #137245) [Link]
For $WORK we needed an inexpensive router with high IPSec throughput, and the option we settled on was a Mikrotik box, which runs some form of Linux but the crypto offload hardware is proprietary.
Even when it comes to standard distros, though, dropbear added support for Ed25519 and RSA+SHA-2 only very recently, so those aren't yet supported in stable OpenWRT.
OpenSSH 8.6 released
Posted Apr 22, 2021 20:30 UTC (Thu) by Sesse (subscriber, #53779) [Link]
Why do you believe they are running Linux in the first place?
OpenSSH 8.6 released
Posted Apr 22, 2021 20:32 UTC (Thu) by pabs (subscriber, #43278) [Link]
I was asking about what they *can* run rather than what they ship with.
Openssh Server Config Download
OpenSSH 8.6 released
Posted Apr 22, 2021 20:36 UTC (Thu) by Sesse (subscriber, #53779) [Link]
They can run firmware images signed by the vendor, using their proprietary OS, period. They can not run Linux, there is no effort underway to port Linux to them, the hardware (which is custom, highly nontrivial, and intertwined with the software) is not documented, and to be honest, I don't think I'd want Linux on them either.
OpenSSH 8.6 released
Posted Apr 22, 2021 21:00 UTC (Thu) by pabs (subscriber, #43278) [Link]
There are folks trying to change this, here are a few of the Debian derivatives I know about, I think they mostly do enterprise stuff though:
https://wiki.debian.org/Derivatives/Census/VyOS
https://wiki.debian.org/Derivatives/Census/DANOS
https://wiki.debian.org/Derivatives/Census/CumulusLinux
https://wiki.debian.org/Derivatives/Census/OpenNetworkLinux
OpenSSH 8.6 released
Posted Apr 20, 2021 13:32 UTC (Tue) by itvirta (guest, #49997) [Link]
Removing things from the enabled-by-default list doesn't prevent enabling them when needing to talk to ancient

equipment. It wasn't too long ago I used something like 'ssh -c3des' (or even 'ssh -1') to connect to some such
relic. Per-host settings for Ciphers, Protocol, KexAlgorithms and such in '.ssh/config' also help if you need to do
that often.
The problem is downgrades that can happen automatically, within the the default-enabled settings.
(And downgrading to telnet probably doesn't fit there.)
OpenSSH 8.6 released
Posted Apr 20, 2021 18:54 UTC (Tue) by lamikr (subscriber, #2289) [Link]
If I create the ca.key and pem file with OpenSSL 1.1.1k which I believe is the latest release by using typical command shown in many examples:
openssl req -new -x509 -keyout ca.key -out ca.pem -days 45 -config ./ca.cnf
and then check the cipher used with command:
openssl asn1parse -in ca.key
From the output I can see that the des is still used as a cipher:
64:d=4 hl=2 l= 8 prim: OBJECT :des-ede3-cbc
Shouldn't openssl use something more secure by default?
OpenSSH 8.6 released
Posted Apr 20, 2021 19:41 UTC (Tue) by tamiko (subscriber, #115350) [Link]
> Shouldn't openssl use something more secure by default?It should. But this is entirely orthogonal to openssh changing it's default-enabled cipher set.
OpenSSH 8.6 released
Posted Apr 22, 2021 17:42 UTC (Thu) by jschrod (subscriber, #1646) [Link]
The topic here is complete removal, not removal from the enabled-by-default list.
OpenSSH 8.6 released
Posted Apr 22, 2021 10:30 UTC (Thu) by jezuch (subscriber, #52988) [Link]
Openssh Server Configuration For Windows 10
Doing something once every couple of years does not strike me as 'incessant', and moaning about this particular one strikes me as denying reality. The reality of security is that the attacks only get better and time is *not* your friend. Thus key rotation should be routine, not an inconvenient thing you're forced to by external events.
What is sad is that the designers of the SSH protocol were also denying this reality. Support for *automatic* key rotation and upgrade should have been designed into the protocol from the start. It is not, so everyone has to do it manually (or automating it themselves) and everyone suffers and security suffers even more. So, in the end, I don't really blame you for moaning.
Obviously I have a couple of decades of hindsight to benefit from so I guess it turns me into a smart-ass at this point :)
Openssh Server Configuration
OpenSSH 8.6 released
Posted Apr 22, 2021 11:42 UTC (Thu) by pizza (subscriber, #46) [Link]
> Support for *automatic* key rotation and upgrade should have been designed into the protocol from the start.Windows 10 Openssh Config
Absolutely!
I'm in a situation where I have a gerrit instance using one of these these problematic host keys (generated back in 2011), mostly hit by tools (ie git) on systems I don't control. I can't replace that problematic key with a stronger one without requiring manual intervention on every single client that hits this thing. Bleh.
OpenSSH 8.6 released

Posted Apr 22, 2021 13:59 UTC (Thu) by grawity (subscriber, #80596) [Link]
I think that clients should not completely remove support for no-so-old algorithm but instead require an extra option like '--insecure' or something like this.
I somewhat agree with this, but, fortunately, OpenSSH isn't the only SSH client for Linux. PuTTY (specifically the 'plink' command) is actively maintained and has support for everything under the sun, from Ed448 to SUPDUP.



 equipment. It wasn't too long ago I used something like 'ssh -c3des' (or even 'ssh -1') to connect to some such
equipment. It wasn't too long ago I used something like 'ssh -c3des' (or even 'ssh -1') to connect to some such

Comments are closed.